Cyber Future Summit is a unique event focusing on action towards building a collaborative and trusted global platform for cyber. The Summit is presented by CFF in an interactive and leadership exercise format, where the leaders and futurists from different walks of life will gather not only to share ideas of building a trusted cyber but actually creating definite actionable guidance and frameworks towards Trusted Cyber and take it back to their respective constituencies.








Our Speakers

Joseph Cheung
Our Summit Provisional Agenda*
The detailed agenda for the Cyber Future Summit is in the works. Be sure to check back soon for updates on our exciting lineup of speakers and topics.
| Session | Time | Location | Topic | Speakers | |||
|---|---|---|---|---|---|---|---|
| Breakfast | 8:00 AM -9:00 AM | In Person | Buffet | ||||
| D1.S01 | 9:00 AM – 9:15 AM | Ballroom | Welcome and Introduction |
| |||
| D1.S02 | 9:15 AM – 9:45 AM | Ballroom | Fireside Chat: SEC regulatory and enforcement action and engagement of CISOs |
| |||
| D1.S03 | 9:45 AM – 10:30 AM | Ballroom | Elevating the CISO Profession: Standards and Accreditations | Moderator:
| |||
| D1.S04 | 10:30 AM – 11:15 AM | Ballroom | Leading the future of Cybersecurity Industry: The Professional Association of CISOs | Moderator:
| |||
| D1.S05 | 11:15 AM – 12:00 PM | Ballroom | Safeguarding the CISO: Addressing Personal Liabilities and Asset Protection | Moderator:
| |||
| D1.B02 | 12:00 PM – 1:00 PM | Arena | Lunch | ||||
| D1.S06 | 1:00 PM – 1:30 PM | Ballroom | CISA’s Role in National Cybersecurity Defense |
| |||
| D1.S07 | 1:30 PM – 2:15 PM | Ballroom | Securing Critical Infrastructure: Cybersecurity in Energy and Public Utilities |
| |||
| D1.S08 | 2:15 PM – 3:00 PM | Ballroom | Protecting the Ecosystem from Concept to Care |
| |||
| D1.B03 | 3:00 PM – 3:30 PM | Ballroom | Afternoon Break | ||||
| D1.S10 | 3:30 PM – 4:15 PM | Ballroom | Secure AI for the Future: CFF RSAIF Framework |
| |||
| D1.S11 | 4:15 PM – 5:00 PM | Ballroom | Enhancing Cyber Resilience through Information Sharing |
| |||
| D1.S13 | 5:00 PM – 5:15 PM | Ballroom | Conclusion and Takeaways |
| |||
| D1.S14 | 5:15 PM – 6:15 PM | Ballroom | |||||
| D1.B04 | 6:15 PM – 7:15 PM | Foyer | Speakers Dinner |
| Session | Time | Location | Topic | Speakers | |||
|---|---|---|---|---|---|---|---|
| Breakfast | 8:00 AM – 9:00 AM | In Person | Buffet | ||||
| D2.S01 | 9:30 AM – 9:45 AM | Ballroom | Welcome & Kick-off |
| |||
| D2.S02 | 9:45 AM – 10:35 AM | Ballroom | The Geopolitical Landscape and the Need for Cross Sector Collaboration in Cyber Defense – a Not for Profit Perspective |
| |||
| D2.S03 | 10:25 AM – 11:00 AM | Ballroom | Resources for Cyber Workforce Development | Moderator:
Panelists:
| |||
| D2.S04 | 11:10 AM – 11:55 AM | Ballroom | Strengthening National Security in the Cyber age |
| |||
| D2.B02 | 11:55 AM – 12:55 PM | Arena | Lunch | ||||
| D2.S05 | 12:55 PM – 1:35 PM | Ballroom | Executive Statement National Security and Cyber Defense |
| |||
| D2.S06 | 1:35 PM – 2:20 PM | Ballroom | The Age of AI and Misinformation: Challenges and Preparation |
| |||
| D2.S07 | 2:20 PM – 3:05 PM | Ballroom | Cyber Trends in Colorado |
| |||
| D2.S08 | 3:00 PM – 3:30 PM | Ballroom | Wrap Up |
|
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| #101 | Welcome and Introduction to the 8th Annual Cyber Future Summit | Valmiki Mukherjee |
| #102 | Welcome to Ottawa – Canada’s Cybersecurity Capital | Rob Davidson, Mark Tse |
| #103 | Unraveling the Cyber Threat Landscape in the Healthcare Industry | Valmiki Mukherjee (Moderator); Errol Weiss, Paul Connelly |
| #104 | Effective Stewardship of Cybersecurity Risk and Avenues for Improvement in Maritime infrastructure | Mike Wilkes (Moderator); Greg Enriquez, Renee Guttman |
| #105 | Maritime Cyber Security and the Canadian Coast Guard: Progress through Partnership | Tanya Alvaro. |
| #106 | Cyber security Workforce: Global Brainstorm to Overcome Talent Shortages, Bridge Confidence Gaps, Innovate Pipeline Strategies | Gordon Pelosse (Moderator); Sheena Bolton, Ron Culler, Joel Rasmus |
| Lunch on | ||
| #112 | International Partnerships to Secure Cyber-Critical Infrastructure in Ukraine and Global Silent Cyber Conflicts | Tom Callahan (Moderator); Kirill Goncharuk, Chris Holden, Joel Rasmus |
| #113 | Insights from the CFF Cyber Board Book: | Valmiki Mukherjee (Moderator); Avani Desai, Danil Kerimi, Mark Orsi |
| #114 | Innovation Ecosystem: | Phil Englert (Moderator); David Guffrey, Dmitry Raidman |
| Afternoon Break | ||
| #116 | Safeguarding Energy Infrastructure: Fortifying Energy Sources and Public Utilities | Valmiki Mukherjee (Moderator); Caroline Cameron, Tom Miller |
| #117 | The Modern CISO: How to Thrive and Not Just Survive the Demanding Role | Valmiki Mukherjee (Moderator); George Al-Koura, Rex Booth |
| #118 | Global Cyber Resilience: Strategic Intelligence from the Insurance Industry | Valmiki Mukherjee, Bryan Hurd |
| #119 | Monday Wrap-Up / Tuesday Preview | Valmiki Mukherjee, Katherine Thompson |
| Networking Reception |
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| #221 | Day 2 Kick-Off | Valmiki Mukherjee |
| #222 | Executive Presentation: | Kirill Goncharuk |
| #223 | Cyber Talent: Where We Are and Where We Need To Be | Katherine Thompson (Moderator); Ron Culler, Jeannette Jarvis, Whit Goodwin |
| Morning Break | ||
| #224 | Automotive Security: The Crucial Need to Accelerate Investment | Katherine Thompson (Moderator); Faye Francy, Divyanshu Kamboj, Cris Sinnott |
| #225 | Responsible, Secure AI Framework Development: What Does Good AI Look Like? | Valmiki Mukherjee (Moderator); Pamela Gupta, Maryam Haghighi, Somaieh Nikpoor, Errol Weiss |
| Luncheon | ||
| #232 | Supporting Cyber Security of Smaller Nations with Increasing Attacks on Critical infrastructure | Maggie McDonough (Moderator); Tom Callahan, Jeannette Jarvis, Steph Shample |
| #233 | Industry Support for Securing Humanitarian Efforts During Challenging Economic/Geopolitical Times | Tom Callahan (Moderator); Danil Kerimi, Maggie McDonough |
| Afternoon Break | ||
| #235 | Curbing Cyber Crime via Law Enforcement and Private Sector Collaboration | Don Codling (Moderator); Brian Abellera, J.D. Bradley, Sima Ghafghaichi, Dawn Morris-Little, Shan Smith |
| #236 | Closing Keynote | Valmiki Mukherjee |
| Networking Reception |
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| Registration | Registration | |
| Session 1 | Welcome to Cyber Future Summit 2022 |
|
| Session 2 | Port San Antonio – Open for Innovation! |
|
| Session 3 | Securing Digital Innovation in Manufacturing |
|
| Session 4 | Healthcare and Medical Hour |
|
| Session 5 | Securing next gen applications – A community Approach |
|
| Break @ Foyer | ||
| Session 6 | Emerging Technology Hour |
|
| Session 7 | National Security Hour |
|
| Session 8 | Cyber Policy in a dynamic geopolitical environment and the Public Private Partnerships |
|
| Session 9 | Day 1 Takeaways & Conclusion |
|
| Session 10 | Innovation Showcase Experience |
|
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| Registration | Registration | |
| Session 0 | Day 2 Kick off | |
| Session 1 | Updates from Ukraine Leaders | |
| Session 2 | Deciphering the workforce conundrum |
|
| Session 3 | Securing Defense Innovation |
|
| Session 4 | Small business Cybersecurity |
|
| Session 5 | Lone Star State of Cyber |
|
| Session 6 | A Primer for Vendors and Buyers: Business Decisions and Third Party Risk Management |
|
| Lunch @ Foyer | ||
| Session 7 | Executive Keynote |
|
| Session 8 | Essential Cybersecurity Program Considerations for Board and C-Suite |
|
| Session 9 | CMMC: The Journey Continues |
|
| Session 10 | Building a cyber resilient business |
|
| Session 11 | Critical Infrastructure Security – From Policy to action |
|
| Break @ Foyer | ||
| Session 12 | Emerging Technology |
|
| Session 13 | Privacy and Consumer Data Protection |
|
| Session 14 | Office of the National Cyber Director – Cyber Workforce and Education Imperatives |
|
| Session 15 | US DoL Cybersecurity Apprentice Program the Progress in 2 Years |
|
| Session 16 | Cybersecurity education continuum – building a long term pipeline |
|
| Session 17 | Day 2 Conclusion |
|
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| Registration | Registration | |
| Session 0 | Day 3 Kick off |
|
| Session 1 | Securing Ukraine telecom infrastructure |
|
| Session 2 | Driving cyber talent forward with Dan Vigdor |
|
| Session 3 | San Antonio – Cyber City – Mayor’s Remarks* |
|
| Session 4 | Next Generation of Cyber talent |
|
| Session 5 | Cybersecurity early education, Ethics, and Best Practices |
|
| Lunch @ Foyer | ||
| Session 6 | Resources and Models for Cyberworkforce development |
|
| Session 7 | C-Suite and Board Engagement for Cyber Resilience |
|
| Session 8 | Securing Innovation in Aerospace Tech |
|
| Session 9 | Cyber Apprenticeship Program with DoL (Remarks) |
|
| Break @ Foyer | ||
| Session 10 | The Crypto Debate – Concerns v. Opportunities |
|
| Session 11 | Cyber security Emerging Tech Debate |
|
| Session 12 | Cyber security Talent v. Automation |
|
| Session 13 | Kaleb Worku’s impressive journey as student in cyber security |
|
| Session 14 | Cyber Insurance in a dynamic threat environment |
|
| Session 15 | Conclusion of Summit |
|
| Session | Theme | Speakers |
|---|---|---|
| Session | Theme | Speakers |
| Registration | Registration | |
| Session 1 | Introduction and welcome remarks |
|
| Session 2 | Critical Infrastructure Security
|
|
| Session 3 | Critical Infrastructure Security
|
|
| Break @ Foyer | ||
| Session 4 | Supply Chain Security
|
|
| Session 5 | Application and Product Security
|
|
| Session 6 | Cybersecurity Strategy
|
|
| Session 7 | Capacity Building
|
|
| Session 8 | Day 1 Conclusion |
|
| Session | Theme | Speakers |
|---|---|---|
| Theme | Speaker | Session Video |
| Introduction and welcome remarks |
| |
| Israel Cyber Hour |
| |
| Cyber Capacity and Talent Development |
| |
| United Kingdom Cyber Hour |
| |
| Small Business Cybersecurity |
| |
| Defeating Ransomware Attacks in the Public Sector |
| |
| Cloud Security and its relation to Critical Infrastructure Security |
| |
| Australia Cyber Hour |
|
| Session | Theme | Speakers |
|---|---|---|
| Theme | Speaker | Session Video |
| India National Cyber Hour |
| |
| Cyber Peace and Warfare |
| |
| Cyber Law, Due Process, Arbitration and Mediation |
| |
| Critical Infrastructure Security |
| |
| Cyber Capacity and Talent – For K-12 Systems |
| |
| Canada Cyber Hour: Building out Canada’s Innovation Ecosystem |
| |
| Recovering from Economic Crisis through Cyber |
| |
| Emerging Tech/InnovationX Entrepreneurship |
| |
| Higher Cybersecurity |
|
| Session | Theme | Speakers |
|---|---|---|
| Theme | Speaker | Session Video |
| Cyber Resiliency and the Role of Organizational Leaders in Supporting a Resilient Business |
| |
| Emerging Tech/InnovationX Entrepreneurship |
| |
| Third Party Risk Management and Supply Chain Security |
| |
| Cyber Capacity and Talent – For K-12 Systems |
|
Secure Your Room for CFS 2025!
As a valued speaker at the Cyber Future Summit 2024, we are pleased to offer you a limited number of rooms at the George W. Bush Presidential Center in Dallas, TX on October 27-28th. Rooms are expected to fill up quickly, so please book your room as soon as possible to ensure availability.
Click the button below to book your slot.
Participate in Cyber Future Summit 2025 | 27 - 28 October, 2025
- General Admission
$895
From JUL 1 2024
- 3 Days in person
-
Access to all sessions
and opportunities
- Special Category
$195
- 3 Days in person
-
Government/Academia/
Military - Access to all sessions
- General Admission
$895
From JUL 1 2024
- 3 Days in person
-
Access to all sessions
and opportunities
- Special Category
$195
- 3 Days in person
-
Government/Academia/
Military - Access to all sessions
Watch 2023 Sessions
Our Valued Sponsors






Regional Premium Sponsor

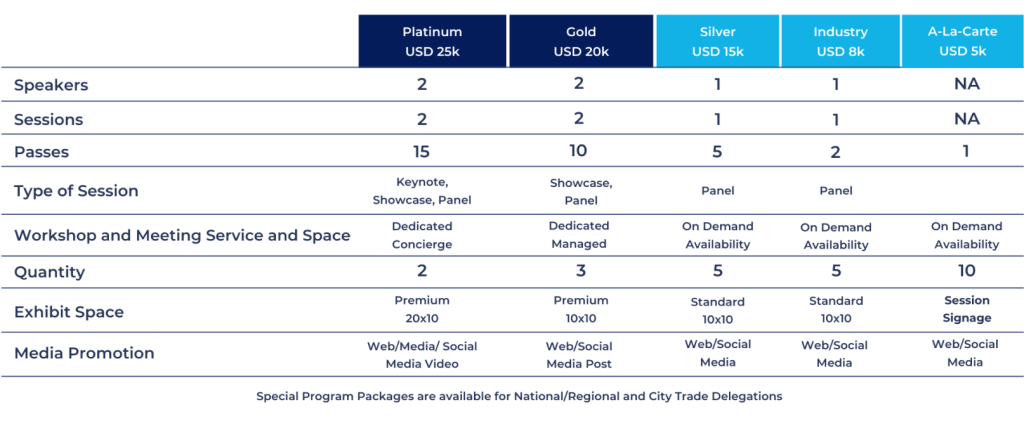
Limited Sponsorship Opportunities Available!
Check Out Details Here
Submit your sponsorship proposal to Program Director or submit your sponsorship form below
Explore Colorado Springs, CO
Planning your Visit to Colorado Springs, CO?
Check out the Official Vacation Planner for Colorado Springs and the Pikes Peak Region to help plan your stay!










































